- Platform
Platforms
- Solutions
- Industries
Industries
- Why FortifyData
Why FortifyData
"This is an excellent starting point for any organization that wants to get serious about their cyber risk management. The system has the capability to grow as you become more sophisticated in your use"
IT Director
Services Industry - Company
Company
- Partners
Partners
- Resources
Resources
Third-Party Risk Management
(TPRM) Based on Live Data
Gain visibility into the cyber risks of your third parties with continuous assessments of their external assets. We conduct real-time attack surface assessments to identify and prioritize vulnerabilities, so you and your third parties can reduce cyber risk. Our technology assessment data is used in conjunction with auto-validated questionnaires for a 360° view of risk.
Patented Risk Score Modeling and Configuration
See Beyond Traditional Risk Ratings
See beyond traditional risk ratings and take control by Scaling the weighting of specific risk scoring criteria related to a group of, or specific third parties.
FortifyData enables you to evaluate prospective vendors to understand data sharing risks, business continuity concerns and their overall cyber hygiene. For existing vendors, you can continuously monitor their evolving attack surface and compliance with your third-party risk management program.
Quickly identify your most vulnerable third parties and create action plans for more focused and collaborative remediation.

Third-Party Questionnaire Management
Keep up to date on the compliance of your suppliers with your policies, and quickly identify vendors that do not comply. Get the full picture of external vulnerabilities at your third parties with our auto-validated questionnaires that leverage the live assessment data conducted on their environment. This provides you with the answers you need more quickly (in the time to run an assessment) than a manual questionnaire process. Create custom questionnaires that are specific to each vendor. Easily assign tasks and collaborate and track questionnaires with our task management capabilities.
Continuous Third-Party Risk Exchange
Speed up vendor evaluations by spending less time reviewing questionnaires with FortifyData’s Questionnaire Exchange. Participants instantly access shared validated cyber risk assessments and questionnaires, allowing you to quickly make risk based decisions.
Vendor questionnaire responses are auto-validated for contradictions through our continuous technical assessments, allowing you to accurately vet and monitor third party risk changes over time.
Read our Next Generation Third-Party Risk Management Whitepaper
Learn about the next generation of Third-Party Risk Management platforms that provide intelligence based on assessments, in addition to open source intelligence data.

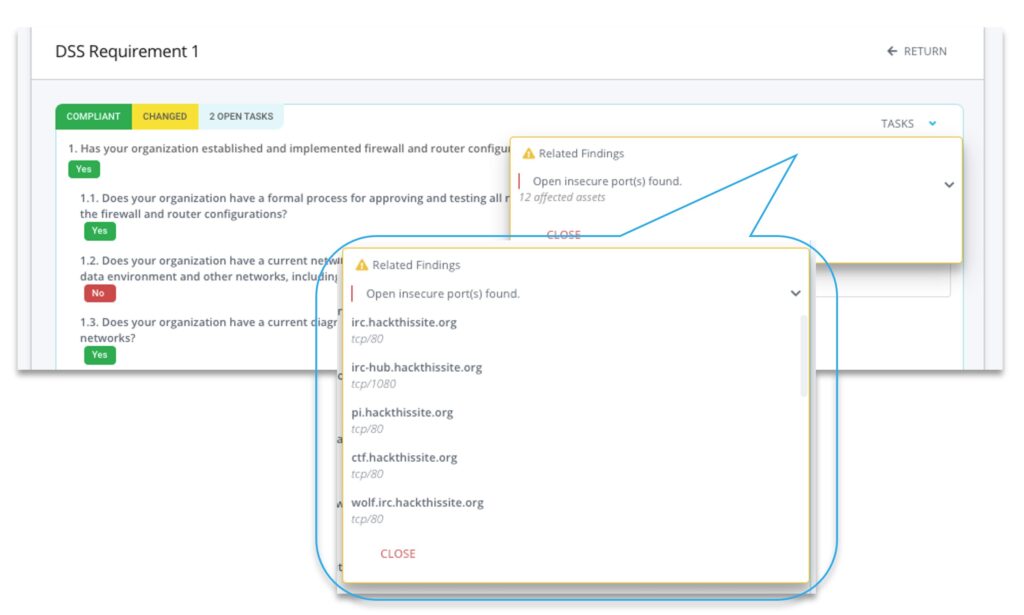
Compliance Gaps and Reporting
Instantly measure compliance levels against your organizations standard questionnaire or well-known frameworks such as ISO27001, PCI DSS, NIST, CSF, HIPAA, SOC2 and more. With our automated compliance validation, you can discover gaps in controls, allowing you to spend less time reviewing evidence.
Compliance Findings
Related Control Findings for companies with assigned questionnaires
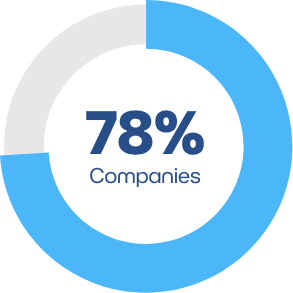
Open Ports
Open, insecure communication ports found.
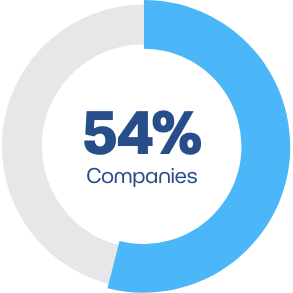
Vulnerabilities
TLS/SSL Vulnerabilities Found.
Get in Touch
To learn more about how to protect your business from cyber risk, contact us directly.
